Understanding Different Types of Key Cards and How To Choose
Dive into our extensive guide on key cards. Unveil the different types of key cards and their unique features, benefits, potential disadvantages, and solutions for common issues.
In the modern world, traditional keys have largely given way to more advanced access control methods – and key cards stand at the forefront of this shift. These handy tools come in various forms, including RFID, Smart, NFC, and Magnetic Stripe cards, each with unique features and advantages.
This guide aims to comprehensively understand key cards, their types, how they work, their advantages, solutions, and frequently asked questions.
How do key cards work?
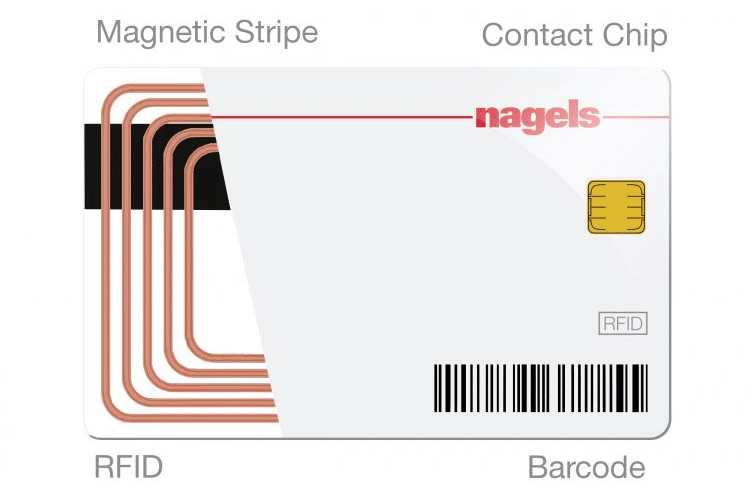
Key cards contain encoded data that a card reader reads. Depending on the card type, this data may be stored on a magnetic stripe, in a microchip, or an embedded RFID tag.
When the keycard is presented to the card reader, the reader reads the data and compares it with the stored information. If the data matches, the door unlocks. The specifics of how this works can vary depending on the keycard type.
In all these cases, the card reader is connected to an access control system that determines whether the data read from the card allows access.
This could be a simple system that only allows access to cards with specific data or a more complex system that checks a database to determine access based on time of day, location, etc. The system can also record when and where each card is used, providing an audit trail.
Types of Key Cards: Benefits, Advantages and Application
Generally speaking, the key cards referred to today are basically electronic key cards.
Electronic key cards are a type of key card that uses electronic data to provide access to a secured area. These cards have an embedded microcircuit (usually a microchip) that contains electronic memory and possibly an embedded integrated circuit (IC). They interact with a reader through contact or contactless methods to grant access.
Here are the main types of electronic key cards:
- RFID Key Cards
- Smart key cards
- NFC Key Cards
- RFID Vs. Smart Vs. NFC Key Cards
- Magnetic Stripe Cards
- Optical Cards
- Wiegand Cards
- Hybrid Cards
- Dual-Interface Cards
RFID Key Cards
RFID, or Radio Frequency Identification cards, use a built-in radio transmitter and receiver. When the card comes close to a reader on the RFID hotel door lock, the reader sends a radio signal to the card, which responds with its stored data. This technology allows contactless use, which can be more convenient and reduce wear and tear.
RFID Key Cards Technology
Radio Frequency Identification (RFID) key card technology uses radio waves to identify and track objects. The system has an RFID tag, a reader, and an antenna. RFID cards contain an integrated circuit and an antenna, which are used to transmit data to the RFID reader.
The reader then converts the radio waves to a more usable form of data. Information collected from the tags is then transferred through a communications interface to a host computer system, where the data can be stored in a database and analyzed later.
Applications
RFID key cards have a wide range of applications, including:
- Access Control: They are used in buildings, offices, and gated communities for secure access control. Only people with the correct RFID card can access specific areas.
- Hotels: RFID cards are used as room keys in the hospitality industry.
- Public Transport: RFID cards are used in public transportation systems for automated fare collection.
- Identification: In some workplaces, RFID cards serve as ID cards.
- Payment Systems: They are used in contactless and electronic toll collection systems.
Encoding
To encode RFID key cards, you need an RFID writer or encoder and the data you want to encode. The process involves using the RFID writer to send the data to the chip embedded in the card via radio waves. The data is then stored on the chip and can be read by an RFID reader.
Verifying the data after writing is important to ensure it has been correctly encoded. The specific encoding process and equipment may vary depending on the frequency and protocol of the RFID card. Some cards are read-only, while others can be rewritten with new data.
RFID key cards benefits:
- Contactless: RFID key cards are contactless and can be read from a distance, making them convenient.
- Durability: They are more durable than magnetic stripe cards as they do not require physical contact with the reader.
- High data capacity: RFID cards can store a large amount of data compared to other similar technologies.
- High speed: RFID cards can be read quickly, making them suitable for applications where speed is important, like public transport.
Limitations
- Cost: RFID cards and readers can be higher than other technologies, such as barcodes or magnetic stripes.
- Privacy concerns: Since RFID cards can be read from a distance, there is a risk of unauthorized reading, leading to privacy concerns.
- Interference: RFID can suffer from interference from other radio frequency devices, leading to inaccurate readings.
- Limited Range: While RFID cards do not require contact, the range at which they can be read is still limited. This is particularly the case with passive RFID cards that don’t have their power source and instead get power from the reader’s signal.
- Compatibility: There is a lack of universal standards in RFID technology, which means that different systems may not be compatible.
Proximity keycards
These use Radio Frequency Identification (RFID) technology to communicate with a reader without physical contact. This makes them more durable than magnetic stripe cards, as there is no physical contact to wear them out. They can also be used while remaining inside a wallet or purse.
Proximity cards typically work on a 125 kHz LF band. These are read-only, contactless cards or badges that can store limited information.
Typical proximity cards can be read up to 15 inches (<50 cm). Their advantages, limitations, and way of working are the same as RFID cards, except that they do not need to be inserted into a reader.
Smart key cards
These contain a microchip and can store much more data than other types of cards. They can also use encryption to provide additional security. They come in two types: contact and contactless. Contact smart cards need to be inserted into a reader, while contactless smart cards can communicate with the reader wirelessly, similar to proximity cards.
Smart Key Cards Technology
Smart key cards are a type of RFID card that has an embedded microprocessor. They can store and process a large amount of data, carry out their on-card functions (like encryption and mutual authentication), and interact intelligently with a smart card reader.
Security
Smart key cards are more secure than traditional magnetic stripe cards. They can employ encryption and secure communications protocols to protect the data stored on them. In addition, they use mutual authentication, meaning the card and the reader authenticate each other before data is exchanged. This makes them very difficult to clone or counterfeit.
Applications
Smart key cards are used in a variety of applications, including:
- Access Control: Similar to RFID cards, they are used in buildings and offices for secure access control.
- Hotel keys: Many hotels use smart key cards as room keys.
- Public Transportation: Contactless smart key cards are used in public transportation systems for automated fare collection.
- Payment Systems: They are used in contactless payment systems.
- Identification: In some workplaces, smart key cards serve as ID cards.
Encoding
Smart key card encoding requires specialized equipment that can communicate with the embedded microprocessor on the card. The encoding process involves writing data to the card and setting up the necessary security features, such as encryption keys and authentication protocols.
Smart key cards benefits:
- High Security: Encryption, mutual authentication, and secure communications protocols make smart key cards very secure.
- Large Data Capacity: Smart key cards can store a large amount of data.
- Versatility: They can be used for multiple applications. For example, a single smart key card could be used for building access control, payment, and identification.
Disadvantages
- Cost: Smart key cards and the necessary encoding equipment can be more expensive than other key cards.
- Compatibility: Similar to RFID, there is a lack of universal standards in smart card technology, which means that different systems may not be compatible.
- Reader Requirements: Smart key cards require a reader that can communicate with the embedded microprocessor, which may limit their use in environments where such readers are not available.
- Privacy Concerns: Though they are more secure, smart key cards can still be subject to unauthorized reading and tracking, leading to potential privacy concerns.
NFC Key Cards
NFC, or Near Field Communication, is a type of RFID that works over very short distances – typically just a few centimeters. NFC is often used for mobile payments but also key cards.
NFC Key Cards Technology
Near Field Communication (NFC) is a short-range wireless connectivity technology that enables simple and safe two-way interactions between electronic devices. NFC key cards use NFC technology to exchange data with a reader when brought into proximity (usually a few centimeters). NFC operates at 13.56 MHz and transfers data up to 424 Kbits/second.
Applications
NFC key cards have a wide range of applications, including:
- Access Control: They are used in buildings, offices, and gated communities for secure access control.
- Hotels: NFC cards are used as room keys in the hospitality industry.
- Public Transport: NFC cards are used in public transportation systems for automated fare collection.
- Mobile Payment: They can be used for mobile payment applications, like Google Pay and Apple Pay.
- Information Sharing: NFC key cards can be used to share information, like contact details or web links, when tapped against an NFC-enabled device.
Encoding
NFC key cards can be encoded using an NFC encoder, which writes data to the card. The data is stored on an NFC chip embedded within the card. The encoding process involves writing a unique identifier or other information to the card, depending on the intended use.
NFC key cards benefits:
- Convenience: NFC key cards are easy to use — they must be tapped against an NFC-enabled device.
- Versatility: NFC cards can be used for various applications, from access control to mobile payment.
- Communication with smartphones: Unlike other types of RFID, NFC is also used in smartphones, meaning NFC cards can interact directly with most modern smartphones.
Limitations
- Short Range: NFC is very short, typically a few centimeters. This can be a limitation for some applications.
- Power Consumption: While passive NFC key cards don’t consume power, active NFC devices like smartphones or payment terminals can consume significant power when using NFC.
- Compatibility: NFC may not be compatible with older card readers or devices that use other types of RFID.
- Security: While NFC does include provisions for encryption and secure communications, the short range of NFC can be exploited by attackers to eavesdrop on communications or to perform unauthorized transactions. However, the risk is lower than other wireless technologies due to the required proximity.
- Cost: While NFC key cards have decreased, they can still be more expensive than other key cards, particularly for large deployments.
RFID Key Cards Vs. Smart key cards Vs. NFC Key Cards
All three types of cards – RFID, smart, and NFC – use radio frequency technology for contactless data communication. However, they differ in terms of their capabilities, security features, and applications. Here’s a comparison table:
| Feature | RFID Key Cards | Smart Key Cards | NFC Key Cards |
|---|---|---|---|
| Basic Technology | Use radio waves to transmit data. They can be either active (with their power source) or passive (powered by the reader’s signal). | A type of RFID card with an embedded microprocessor. They can carry out their on-card functions and interact intelligently with a reader. | A type of RFID technology that enables two-way interactions between devices within a short range (usually a few centimeters). |
| Security | Basic RFID cards offer limited security features. However, encryption can be added for increased security. | Provide higher security through encryption, secure communications protocols, and mutual authentication. | NFC includes provisions for encryption and secure communications, but the short range can be exploited by attackers for eavesdropping or unauthorized transactions. |
| Data Capacity | It varies depending on the type of RFID card, but generally less than smart cards. | High data capacity due to the embedded microprocessor. | Data capacity is typically lower than smart cards due to NFC’s short communication range and speed. |
| Applications | Used widely for access control, ID cards, toll collection, etc. | They are used for access control, payment systems, ID cards, and more. | They are used for access control, mobile payment, information sharing, and more. |
| Cost | Generally less expensive than smart and NFC cards. | It is more expensive than basic RFID cards due to the embedded microprocessor. | Costs are decreasing but can still be higher than basic RFID cards, especially for large deployments. |
| Compatibility with other devices | RFID readers are required. | Requires specialized readers that can communicate with the microprocessor. | It can interact directly with most modern smartphones and specialized readers. |
| Range | It can be read from a few centimeters to several meters away, depending on the type of RFID card. | Similar to RFID cards, the range depends on the type of smart card but is generally short to ensure secure communication. | A very short range (usually a few centimeters) ensures that communication is only established when devices are intentionally brought close together. |
| Speed | The speed of reading data from an RFID card is generally fast, making them suitable for applications where speed is important. | Communication speed is generally slower than basic RFID due to the processing that occurs on the card. | Data transfer speed is up to 424 Kbits/second. |
| Interference | It can suffer from interference from other radio frequency devices. | Similar to RFID cards, smart cards can also suffer from interference. | Less susceptible to interference due to the very short communication range. |
| Durability | They are more durable than magnetic stripe cards as they do not require physical contact with the reader. | Like RFID cards, smart cards are more durable than magnetic stripe cards. | Like other RFID cards, NFC cards are durable and do not require physical contact with the reader. |
| Privacy Concerns | It can potentially be read from a distance, leading to privacy concerns. | While they offer more security features, unauthorized reading and tracking can still be a concern. | The short range of NFC provides some privacy protection, but unauthorized reading can still occur if an attacker gets close enough. |
Remember that each technology has strengths and weaknesses; the best choice depends on the application’s requirements.
For instance, basic RFID might be the best choice for a low-cost, high-speed toll collection system, while smart cards might be preferred for an access control system that requires high security. On the other hand, NFC could be ideal for a contactless payment system that needs to work with customers’ smartphones.
Magnetic Stripe Keycards
Magnetic Stripe Cards are the same size as a credit card and work by storing data on a magnetic stripe, similar to that on a credit card. They are relatively cheap to produce and can be reprogrammed if necessary. However, they can wear out over time and be damaged by magnets.
Magnetic Stripe Card Technology
Magnetic stripe cards, also known as swipe cards or magstripe cards, have a band of magnetic material embedded on the card’s stripe. This stripe stores data by modifying the magnetism of tiny iron-based particles in the stripe. The magnetic stripe is read by physical contact and swiped through a magnetic reading head.
Applications
Magnetic stripe cards have been widely used in various applications, such as:
- Financial Services: Credit and debit cards use magnetic stripes to store account information.
- Identification: ID cards, driving licenses, and membership cards often use magnetic stripes.
- Access Control: They are used for access control in buildings and offices.
- Hotel keys: Many hotels use magnetic stripe cards as room keys.
Encoding
It would be best to have a magnetic stripe encoder to encode a magnetic stripe card, which writes data onto the stripe. The encoder uses an electromagnetic field to change the magnetism of the particles in the stripe, effectively writing data onto the card.
Magnetic stripe key card benefits:
- Low Cost: Magnetic stripe cards are typically cheaper to produce than RFID, smart, or NFC cards.
- Wide Acceptance: They are widely accepted and used worldwide, especially in financial services.
- Simple Technology: The technology is straightforward to understand, making it simple to implement.
Disadvantages
- Wear and Tear: The magnetic stripe can become demagnetized or scratched with use, leading to the card failing.
- Low Security: Magnetic stripe cards are relatively easy to clone, and their data can be easily read and copied, leading to potential security issues.
- Contact Required: Unlike RFID, smart, or NFC cards, magnetic stripe cards must be swiped through a reader, which requires physical contact.
- Limited Data Capacity: Magnetic stripes can store less data than RFID, smart, or NFC cards.
Optical Key Cards
Optical cards use changes in reflectivity to store data. They can store a lot of data and are highly resistant to tampering, but they require special readers and are more expensive to produce.
Optical Card Technology
Optical cards are a data storage medium that uses optical technology to record and read data. The card’s surface is covered with a layer of optical material that can be altered by a laser to store data. The data is then read by reflecting a lower-intensity laser off the card and detecting the differences in the reflection.
Unlike magnetic stripe cards or RFID cards, optical cards store data in a visible, high-density format similar to CDs and DVDs. The data can be stored in two formats: WORM (Write Once Read Many), which allows data to be written once and read many times, and erasable, which can be rewritten multiple times.
Applications
Optical cards have several applications, including:
- Medical Records: The high storage capacity of optical cards makes them suitable for storing detailed medical records.
- Financial Services: Optical cards can be used for banking and credit cards, where the high capacity can be used for transaction records.
- Identification: ID cards and driver’s licenses can use optical technology for added security and data capacity.
- Document Storage: The high storage capacity can be used for storing large documents or images.
Encoding
Encoding an optical card requires a special device that can emit a laser of the correct intensity to alter the optical material on the card. A similar device reads the card, using a lower-intensity laser and sensors to detect the reflection.
Optical key cards benefits:
- High Storage Capacity: Optical cards can store a large amount of data, much more than magnetic stripe or RFID cards.
- Durability: Optical cards are resistant to magnetic fields, dust, and water, making them more durable than other cards.
- Security: The data on an optical card is difficult to alter or erase without the correct equipment, providing a degree of security.
Disadvantages
- Cost: The cost of producing optical cards and the equipment to read and write them can be higher than other cards.
- Compatibility: Since optical cards require special equipment to read and write, they may not be compatible with systems designed for magnetic stripe or RFID cards.
- Speed: Reading and writing data to an optical card can be slower than other cards due to the high-density storage format.
Wiegand Key Cards
These older cards use embedded wires to store data. Wiegand key cards contain a series of wires embedded in the card, each representing a bit of data. When the card is swiped through a reader, the wires pass through a magnetic field, generating pulses read as data.
They are highly durable and resistant to tampering but are more expensive to produce and cannot store as much data as smart cards. Wiegand technology is largely obsolete now and has been replaced by newer technologies.
Wiegand Effect
The Wiegand effect is a non-linear magnetic effect named after its discoverer, John R. Wiegand. It’s based on using a specially treated (through a process called “Wiegand wire”) ferromagnetic alloy known as Vicalloy.
This alloy has the unusual property of displaying a sharp jump in its magnetic polarity when exposed to a magnetic field of a certain strength. When the polarity changes, a pulse is generated, which can be picked up by a coil. This pulse is the basis of Wiegand data communication.
Applications
Wiegand key cards have been used primarily in access control systems, including:
- Building Access: They can control entry into buildings or secure areas.
- Gate Access: They can enter gated communities, parking lots, or secure locations.
- Industrial Security: They can control certain areas or equipment in industrial settings.
Encoding
Encoding a Wiegand key card involves setting the Wiegand wires in the card to represent the desired data. This is typically a binary code, each wire representing one bit of data. The encoding process is generally done during manufacturing and can’t be changed once set.
Wiegand key cards benefits:
- Durability: Wiegand cards are physically robust and resistant to wear and tear. The Wiegand effect is not affected by dirt, oil, or minor scratches on the card.
- Long Read Range: The Wiegand effect can be read at a greater distance than magnetic stripe cards and often even RFID cards.
- Security: The data on a Wiegand card is difficult to duplicate or modify, providing a high level of security.
Disadvantages
- Cost: Wiegand cards can be more expensive than other cards due to the complexity of the technology and the manufacturing process.
- Limited Data Capacity: Each Wiegand wire in the card represents one bit of data, so the amount of data that can be stored on a card is limited by the physical size of the card.
- Inflexibility: The data can’t be changed once a Wiegand card is encoded.
- Compatibility: Wiegand cards require a specific type of reader, which means they may not be compatible with systems designed for other cards.
Hybrid Key Cards
A hybrid key card is a single card that combines two or more different technologies. These cards are designed to maximize compatibility with a variety of systems and to provide enhanced functionality. For instance, a hybrid key card might contain an RFID chip and a smart card chip or combine NFC technology with a magnetic stripe.
Here are some key points about hybrid key cards:
- Technology: Hybrid cards can incorporate various technologies, such as RFID, smart cards, NFC, and magnetic stripes. They are designed so that each technology operates independently of the others, which means they can be used with multiple systems.
- Applications: The main advantage of hybrid cards is that they can be used for multiple purposes. For example, an employee might use the RFID component of a hybrid card for building access control, the smart card component for secure login to company computers, and the NFC component for contactless payments at the company cafeteria.
- Security: Hybrid cards can offer enhanced security because they can leverage the security features of each incorporated technology. For example, a hybrid card might use the strong encryption capabilities of a smart card chip for certain applications while offering NFC convenience for less sensitive applications.
- Cost: One potential drawback of hybrid cards is cost. Because they incorporate multiple technologies, they can be more expensive to produce than single-technology cards. However, this cost may be offset by the convenience and flexibility of using a single card for multiple purposes.
- Compatibility: Hybrid cards offer the advantage of broad compatibility. Because they can work with multiple systems, they’re a good choice for environments with different systems or for transitioning from an older technology (like magnetic stripe) to a newer one (like a smart card or NFC).
In summary, hybrid key cards offer a versatile solution that can meet various access control, payment, and identification application needs. However, they can be more expensive and complex to manage than single-technology cards.
How to choose the right key cards for your Entry System?
Choosing the right key cards for your entry system depends on various factors, including your needs and constraints. Here are some considerations to help guide your decision:
- Security Requirements: The level of security you need can greatly influence the type of key card system you choose. Smart or dual-interface cards with encryption might be the best choice for high-security applications. If security is less concern, simpler and more cost-effective options like magnetic stripe cards or RFID cards may be sufficient.
- System Compatibility: The key card technology you choose must be compatible with your existing system (if you have one) or with the system you plan to install. Some systems only work with certain types of cards.
- Usage Environment: Consider the environment in which the cards will be used. For example, if the cards will be used outdoors or in harsh environments, you might need particularly durable cards, like Wiegand cards.
- Budget: Cost is always a consideration. More advanced card technologies are more expensive for both the cards and the readers. You’ll need to balance the need for certain features against their cost.
- User Convenience: Consider the convenience of the card technology for the users. Contactless technologies like RFID and NFC are the most user-friendly because they don’t require precise swiping or inserting. However, a dual-interface or hybrid card might be more convenient if users use the cards for other applications (like payment or identification).
- Future-Proofing: Consider whether the technology is likely to remain supported and widely used in the future. Investing in more modern technology (like smart cards or NFC) could be wise if you want your system to remain useful for many years.
- Card Capacity: If you need to store a lot of data on the cards (for example, for multi-factor authentication or for storing user data), you’ll need a card technology with a high capacity, like smart cards or optical cards.
Considering these factors, you can choose the best key card technology for your entry system. It can also be helpful to consult with a knowledgeable professional about access control systems to get their advice based on your situation.
Key card or card key?
“Key card” and “card key” refer to the same object: a card-shaped device that opens an electronic door lock system for hotels. However, the term “key card” is much more commonly used, especially in the context of hotel rooms or secure access areas in a building.
While “card key” isn’t wrong, it’s less standard and might be less readily understood. Unless you’re dealing with a specific context where “card key” is the established term, it’s generally safer to go with “key card.”
Conclusion
As we’ve explored, key cards represent a significant advancement in access control technology. Various types like RFID, Smart, NFC, and Magnetic Stripe cards offer various options for specific needs.
While they have numerous advantages, such as improved security and ease of use, it’s also important to consider potential disadvantages like cost, technological issues, and durability. Understanding these aspects helps make an informed decision about the right key card system for your needs.
Always remember the primary goal of any access control system is to ensure security while offering ease of access to authorized individuals. Key cards play a significant role in achieving this balance.